Generating Custom Wordlists with Kali Linux
In the last post, we looked at cracking WPA2 passwords using an online dictionary attack, which is actually pretty straightforward. However, it is only as good as the wordlist used to crack the hash.
There are a number of wordlists pre-installed on Kali, such as rockyou.txt. But sometimes, it's better to create a specific targeted wordlist. If you know a target's hobbies, pet names, significant dates, or even common typos, a custom wordlist can drastically improve your success rate in cracking their credentials.
Pre-made lists can be huge. Custom lists are smaller, more efficient, and reduce the time spent on irrelevant guesses. Or if you know a password policy requires a certain length, number, or symbol, you can generate lists that strictly adhere to those rules.
In this post I'm going to look at how we can use Crunch to make wordlists based on character sets and patterns, and then pipe that directly into a cracking command.
Crunch
Crunch is great for making wordlists based on character sets and patterns. At its most simple, it can generate a wordlist with minimum length, maximum length, and character set. This command creates all possible 8 character strings using only lowercase letters.
crunch 8 8 abcdefghijklmnopqrstuvwxyz -o 8_char_pass.txt
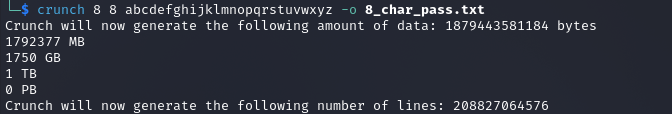
As you can see, this would generate 208,827,064,576 passwords, totalling 1,750GB of data, and that's using only using lowercase letters! Fortunately, Crunch has built in character sets stored in:
/usr/share/crunch/charset.lst
Let's try one now. The full path the list must always be included.
crunch 8 8 -f /usr/share/crunch/charset.lst mixalpha-numeric -o 8_char_pass.txt
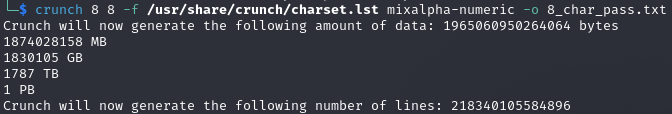
Now we're talking. I'm not even going to try tackling that number. That character set contains all letters, upper and lower case, and numbers. No symbols. Needless to say, I cancelled the command before it started filling my hard drive.
Making Patterns with Crunch
Crunch also has the ability to incorporate patterns into its generation. By using the -t (template) switch, you can keep some parts of the word static while substituting others.
Firstly, we need to know to four primary placeholders.
@ : Lowercase alpha characters
, : Uppercase alpha characters
% : Numeric characters
^ : Special characters
Let's try an example.
crunch 8 8 -t p%ssword
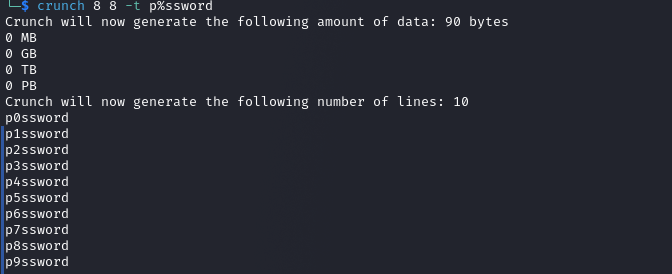
Crunch has cycled through all of the numeric characters in place of the second character. This is useful where you are trying to generate a wordlist of common substitutions.
There are more advanced tools than Crunch that use GPU power to speed up the process, but Crunch is the preferred tool for generating static .txt files or piping character patterns into legacy tools (like aircrack-ng) that lack built-in logic, making it ideal for low-power hardware or fixed-length brute forcing.
Piping Directly into a Cracking Command
What if you're trying to crack a password that is too long to generate a wordlist? Well, instead of storing all the passwords in a list and iterating through it, why not pipe the output of crunch directly into the cracking command. For example:
crunch 8 8 -f /usr/share/crunch/charset.lst mixalpha-numeric | aircrack-ng -w - -b 00:11:22:33:44:55 handshake.cap
Let's break it down.
8 8 : Sets the minimum and maximum length-f [path] [set]: Specifies the charset library and the character set| : The pipe that passes the output to the next command-w - : The hyphen after -w is critical, as this tells the command to 'listen' to the pipe instead of looking for a file-b: The BSSID is mandatory when piping, as aircrack-ng becomes non-interactive when reading from a piped input.
Instead of generating a file, each time Crunch generates a password it will check it against the captured 4-way WPA2 handshake. You can replace aircrack with other hashing cracking tools such as John The Ripper, depending on what you are trying to crack, but concept remains the same.
This is just a concept, and I wouldn't recommend trying this example. That command alone will test 218 trillion passwords, which could take years. But it's a good example of how you can get around the need to produce huge static wordlists and store them.
Comments